Green IT is becoming a key issue for companies. Business processes digitization is leading to an increase in the volume of data bringing the environmental impact on the picture, which is mainly generated through the energy consumption of data centers or data management. Taking this concern into account by companies can also become a serious advantage for the security of their systems. Our data security expert, Alexandrine Demblon shed light on this topic in this article.

What is Green IT?
It is a continuous improvement approach that aims to reduce the environmental, societal & economic impacts of digital technologies. In order to pursue the digital transformation of our societies, it is becoming more and more crucial to think about a more sober, fairer & more efficient approach to our digital uses to minimize their environmental impact.
We now realize that focusing on technical improvements (greater energy efficiency, reduction in the use of materials, etc…) won’t be enough and that we also need to be aware of our digital use consumption. Management tools can already help decision-makers to measure the effects of their choices, for example by integrating quantified environmental settings when evaluating solutions.
6 key steps to combine security & digital sobriety
Reducing the digital environmental impact to its full extent can easily be aligned with recommendations to secure your information systems.
1. Keep control and the knowledge of your applications
An immediate way to increase the security of your information systems is to define an attack surface reduction. The fewer the number of tools you have the more you will limit the number of entry points for potential threats. This also allows you to optimize your software maintenance from a security point of view (patch management) but also to limit its cost.
It is important, both from an environmental and security point of view, to avoid keeping historical applications whose usefulness has become limited or non-existent. The energy & software maintenance costs of these applications are no longer acceptable in our environments.
2. Implement data governance within the company
Data is and will remain at the heart of our concerns. Without it, our business activities would be limited. However, data management represents an ever-increasing risk that can affect a company’s reputation in the event of a data breach. Again, good management practices will help you to mitigate the data confidentiality & ethics risks while minimizing their environmental impact. By avoiding databases duplication and local copies multiplication, we can reduce the risks inherent to security while lowering their storage & transfer costs. Managing data, collecting it, labelling it efficiently & keeping it only for the time required will allow everyone inside the company to access the information that they just need to do their job reliably.
3. Centralize IT services to data centers
Data centers or the Cloud, typically offer better energy efficiency while providing a higher security standard compared to most companies. Not all data centers & cloud contracts are the same. It is important to establish criteria for comparison (whether from a security or environmental point of view) before making a choice.
4. Offer digital documents management solutions
Offering centralized & controlled management of company records allows for more secure & less energy-consuming collaborative work than the systemic sending of documents as attachments. Obviously, this requires an effort to label information & structure document management systems, but in the end, it will bring greater integrity & accuracy while reducing the risk of disclosure of sensitive or confidential information.
5. Master your IT architecture
To better control your environment from a security point of view, you can limit the difficult work of patch management and software maintenance. But did you know this will also reduce the overall ecological impact of the system? All of this can be achieved by knowing your application, not hesitating to decommission what is not used, making choices in terms of technical solutions, limiting different and non-integrated solutions.
6. Develop an integrated vision of development projects
The data collected & stored must be organized in such a way that it can be used in different applications, without having to be re-collected. This is mainly the case for data coming from the IoT where it is possible to share the results of sensors between different applications. This avoids environmental cost in terms of raw materials and energy used and facilitates the security & pseudonymization of data in a single point.
To go further: trust, the new model of our IT systems
In recent years, IT systems security has been widely highlighted, but what companies are expecting is that their IT & data solutions can be used with full trust. This goes far beyond IT security. It is the entire global data management that is impacted.
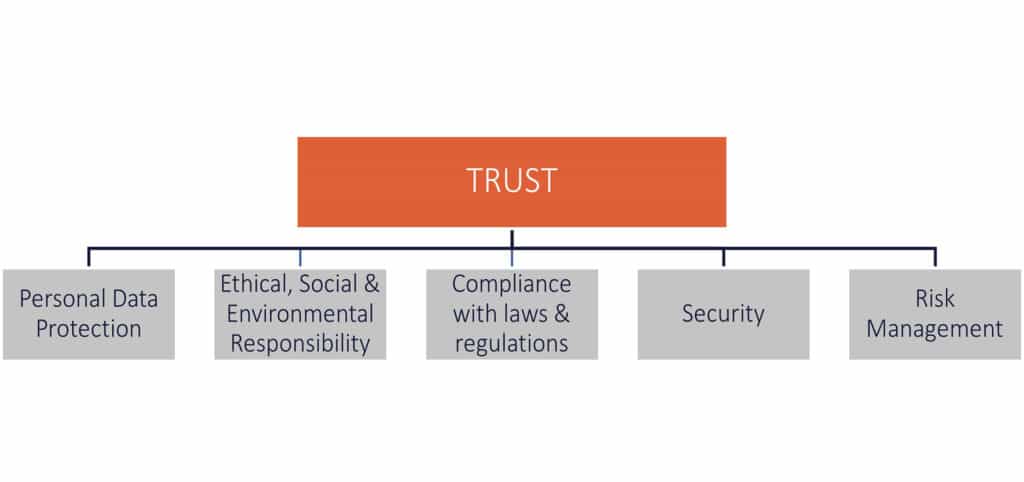
Responsible management of corporate assets is one of the building blocks of this trust. It hast to be an essential part of the strategy of companies. It is made clear the data valorisation goes through Innovation and the combination between sustainability & IA is possible.















Your email address is only used by Business & Decision, the controller, to process your request and to send any Business & Decision communication related to your request only. Learn more about managing your data and your rights.